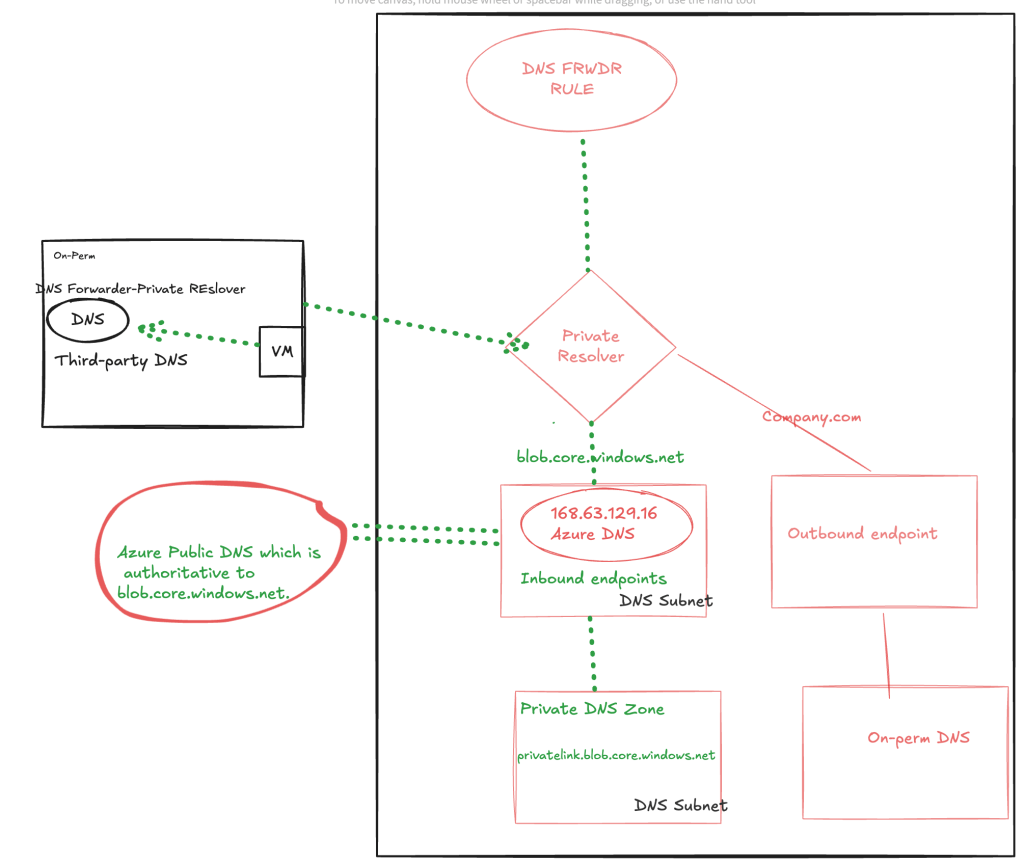
We have a requirement to make sure all the Azure VMs are resolving to our company.com which is our primary DNS domain for on-perm services and also VMs running Azure and from on-perm should resolve azure services like Storage,AKS.
Reference: The Azure DNS Private Resolver service is injected into your Virtual Network and utilises network interfaces for two functions:
Outbound Endpoints – a maximum of five – used to forward resolution requests to destinations within your internal private network (Azure or On-Premises), that cannot be resolved by Azure DNS Private Zones. How the outbound endpoint behaves in respect to forwarding, is dictated by the configuration of the associated DNS Forwarding Ruleset
Inbound Endpoints – a maximum of five – used to receive inbound resolution requests from clients within your internal private network (Azure or On-Premises).
Azure VM resolving the services in on-perm company.com
For the first scenario to access the services hosted in our on-perm from Azure VM, we created the private resolver with outbound rule and if any DNS request to company.com then it will route the traffic to the out-bound rule in the private resolver.
- VM sends a DNS query asking for IP associated to gittest.company.com to Azure Provided DNS 168.63.129.16.
- DNS forwarder rule will route the traffic to outbound endpoint since it is company.com
- As final step outbound endpoint will route it to the on-perm DNS.
- The VM will now be able to access the gittest.company.com via Private Endpoint.
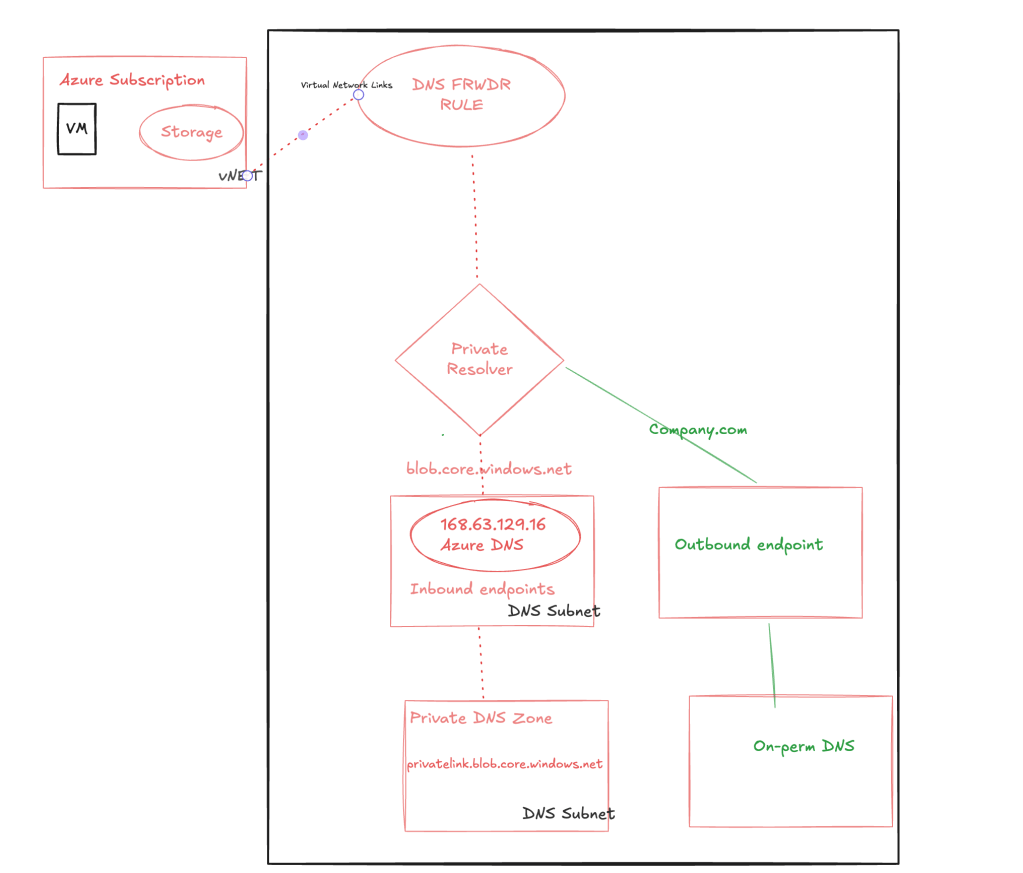
Azure VM resolving the blob.core.windows.net
For the second scenario to access the Azure blob services from the Azure VM, it will route the request to the private resolver in-bound rule and it will resolve to the private DNS zone.
- VM sends a DNS query asking for IP associated to test.blob.core.windows.net to Azure Provided DNS 168.63.129.16.
- Azure Provided DNS sends query to the authoritative DNS Server that hosts blob.core.windows.net zone and process it.
- That authoritative DNS Server responds back to Azure provided DNS in the VNET that with the correct CNAME: test.privatelink.blob.core.windows.net.
- Azure Provided DNS is aware that Private DNS Zone hosts privatelink.blob.core.windows.net zone and can process as host name (A record) from gbbstg1 to its private endpoint IP 10.0.0.5.
- Private DNS zone returns private endpoint IP back to Azure Provided DNS.
- As final step Azure Provided DNS returns private endpoint IP back to the client.
- The VM will now be able to access the Storage Account via Private Endpoint IP.
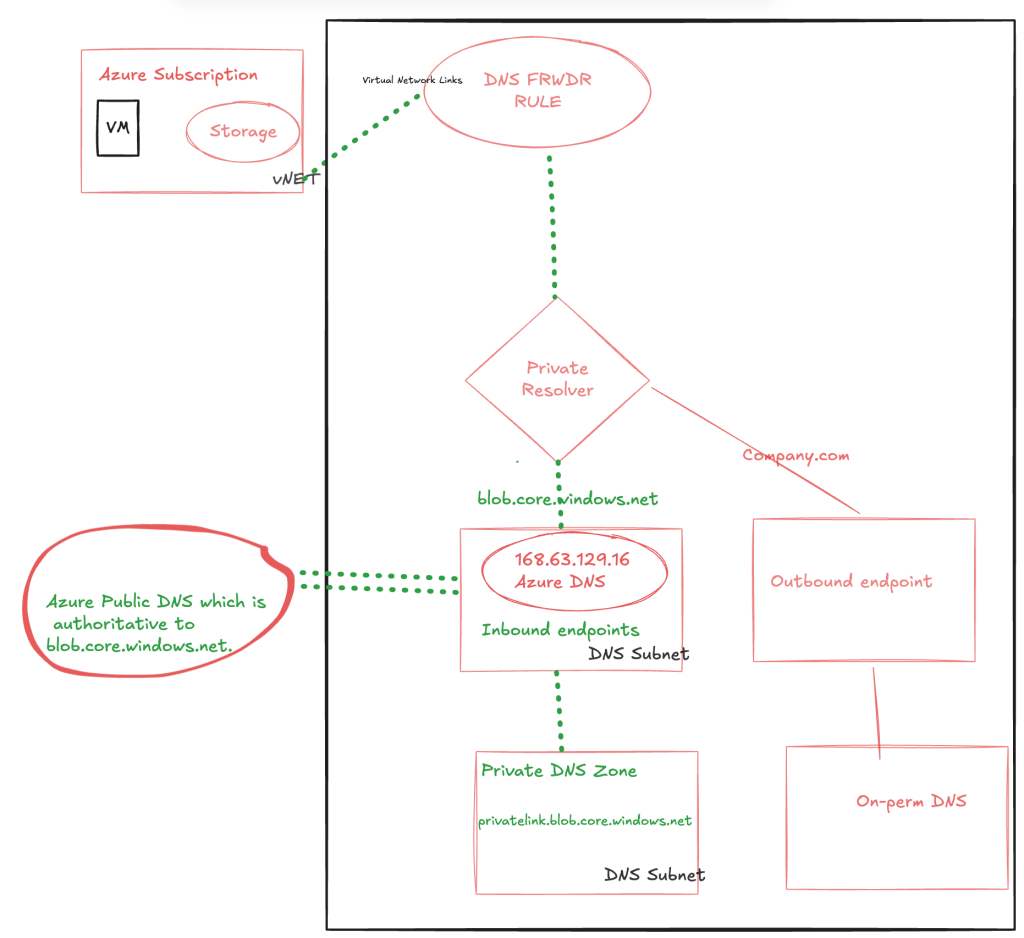
On-perm VM resolving the test.blob.core.windows.net
For the third scenario to access the Azure services like blob from the on-perm.we have configured the forwarder to the private-endpoint IP in our third-part DNS server so any request from the on-perm VM test.blob.core.windows.net, it will forwarde the request to the private resolver and it get resloved.