Pls check my previous blogs for the DSM , Relay Server , vShield End Point , Filter Driver ,DSVA, DSA , SSP Server , Policies and exclusions . In this blog we can see the Trend events and monitoring options..
Deep Security writes information directly into a SQL database. There are no local file or in windows event logs that gets updated when security events are generated.An alternative is we require additional syslog server implementation. If you have a syslog server that can write information to a file, the syslog server can accept syslog information from DSM and write the information to a file for monitoring.
If you configure Deep Security Manager to forward syslog events to an SIEM server, all the events found under Administration >> System Settings >> System Events will be sent to the SIEM Server.
We need to configure it in the policies to send the events to the syslog server so that if any general events in DSM and also Malware events happened in the VM level then it will forward those events to the syslog server and we can monitor it from the logs.
Last week a new free tool called SexiLog has been introduced and its very cool tool and pls see my blog SexiLog for more info and I tested the Trend DSM Events by forwarding it to the SexiLog server which worked with good results.
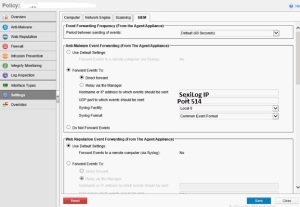
Go to the Administration – System Settings – SIEM
Configure the SexiLog server IP with port 514 in the SIEM settings mentioned above and also under the DSM – Policy ( Select the Policy ) – Settings – SIEM.
Apply the Policy to the VM in the Computers and you can notice the event in the Sexilog Server.
We can see the below Event when we applying the policy to the VM.
Also tested with the Test virus file from the EICAR and when the event happened on the VM , we can see the Graph in SexiLog with the same time stamp.
We can also use Deep Security Manager to configure an SMTP server to send email if any alert occurs. This can be found under the Web Console >> Administration >> System Settings >> Alerts and SMTP tab.
We can choose any particular alert is required the mail notification or not.
Update : This option is default now.
By default Anti-Malware Email alert wont be shown in the DSM and We only need to run the DSM_C.exe command to enable the notification feature.
dsm_c -action changesetting -name “com.trendmicro.ds.antimalware:settings.configuration.eventEmailTabVisible” -value “true”
The “Anti-Malware Email” Tab to configure the notification recipients can be found under Administration >> System Settings.
Trend with vRops.
Trend is the first vendor who have the adapter for collecting the security events in vROPS .We can integrate the Trend DPM with VMware vCenter Operations Manager which give the visibility into security events on the protected VMs from the vCenter Operation Manager console.
Requirements
Trend Micro
• Deep Security Manager v9.x, installed
• Access to the Deep Security Manager web console via a browser
• The Deep Security Manager server must have network access to the vCenter on which VMware
vCenter Operations Manager is installed.
• The Deep Security Management Pack for vCenter Operations package
(DeepSecurityAdapter-1.x-x.pak) must be available to the VMware vCenter Operations
Manager web console in a local directory.
• The Deep Security Management Pack for vCenter Operations certificate importation script (importcert).
Pls download the adapter and the script from the below link
http://downloadcenter.trendmicro.com/index.php?clk=tbl&clkval=4370®s=NABU&lang_loc=1
Trend Micro Deep Security Management Pack version 1.0.0 for vCenter Operations
vCenter Operations Platforms Supported:
- vCenter Operations Advanced Edition Version 5.8.1
- vCenter Operations Advanced Edition Version 5.8.2
- vCenter Operations Advanced Edition Version 5.8.3
- vCenter Operations Advanced Edition Version 5.8.4
Note: Only vCenter Operations Advanced and Enterprise Edition is supported as the management pack adaptor will require the use of Custom Dashboards
Deep Security Manager version Supported:
- Deep Security Manager version 9.0 – build 4017
- Deep Security Manager version 9.5 – build 2456
Not Supported:
Any products and versions not mentioned above
As per the Trend vRealize 6.0.1 version is under development and it will be available only after june.
VMware
• VMware vCenter, installed (up to two vCenters are supported)
• VMware vCenter Operations Manager v5.8.x (Advanced Edition), installed (requires custom
dashboard functionality)
◦ SSH access to the Analytics VM of the vCenter Operations Manager vApp.
Installation Steps
First create the user with Auditor role in DPM.
Enable the SOAP Web Services API in DPM
Administration – Advanced – SOAP Web Service API.
Export the Deep Security Manager Certificate from the Firefox – Options – Advanced – Certificate – Certificate Manager – Servers tab – Export – Select X.509 format – Save the certificate to a file.
Import the Deep Security Certificate and also the import-cert script into vCenter Operations Manager nad pls note use root user and copy it to /root.
Login in to the Analytics VM via Putty as the root user.
Run the below command from the /root
chmod +x import-cert and ./import-cert
And give the full path /root/Deep Security Certificate File.
If you get the below error while running the script then check the binary is enabled in SCP or else just copy the content in the script and paste it in the file directly in the console.
Next install the managment pack in vCOPS.
Oen the vCenter Operations Manager web console and go to the Administration page.
https://vcenter operation manager/admin
On the Update tab, click the Browse button and locate the Deep Security Management Pack for
vCenter Operations package (DeepSecurityAdapter-1.x-x.pak )
Select the Pak file and click Open
Click the Update button
Accept the License and click OK
Wait for Update to complete
Open the VMware vCenter Operations Manager web console interface and go to the Custom Interface page. ( https://<vCenter Operations Manager>/vcops-custom
Go to Environment > Configuration > Adapter Instances
In the Collector menu, select “vCenter Operations Standard Server”
In the Adapter Kind menu, select “Deep Security Adapter”
Click the Add New Adapter Instance icon ( )
In the Add Adapter Instance window, enter the following:
◦ Collector: vCenter Operations Standard Server
◦ Adapter Kind: Deep Security Adapter
◦ Adapter Instance Name: A name for this instance of the Deep Security adapter
◦ Deep Security Manager Host: the hostname or IP address of the Deep Security
Manager – Version : 9 \ Port:4119 \ Auto Discovery:True \ Credential: enter the admin user name and click test.
Since we have upgraded the vROPS to 6.1 , couldn’t test the performance and the below content is taken from the reference link.
Performance Analysis
Trend Micro Deep Security with VMware vCenter Operations Manager v5.8.x (Advanced edition) enables organizations to compare security event activity with performance activity. For example (image 2), we are looking at SQL server (top left) activity. We can see that at the CPU Demand is at 30 percent and then increases sharply to 88 percent. The security event metrics (bottom left) show that the number of security events has also gone up. The detailed information for the security activity (right) shows that these events were due to firewall and malware events being triggered. The jump in security activity and possible threats is likely impacting the performance and causing the spike. The operations team can now inform the security team of their findings and the machines with security events can be examined in detail.
Security Analysis
The Deep Security Heat Map (image 3) quickly lets you see which computers are under attack the most at any given time. Like other vCenter Operations Heat Maps, green indicates fewer events occurring on a particular computer while red indicates more security events triggered. These events can be any of the events in Deep Security Manager; Anti-Malware, Intrusion Prevention, Integrity Monitoring, Firewall, and Web Reputation.
Clicking on the Heat Map will give you the Metric Graph (image 4) for that particular machine. Operations teams can see individual graphs for each type of security event: Anti-Malware, Intrusion Prevention, Integrity Monitoring, Firewall, and Web Reputation. These graphs share critical information such as total events over time and highest/ lowest event counts. This enables a quick overview of the peak time events are being triggered, as well as the specific security events being triggered.
Next topic is just want to share some of the methods to ensure the availability of the DSVA.
We have the options to set the DSVA Heartbeat so that if DSVA have missed communicating to the DSM for the mentioned period then DSM will get an Alarm which can be setup to send mails to the administrator.
Also we can set vSphere Alarms so that if DSVA went down it will create the Alarm for the same.
Next Blog we can see Trend DPM with VDI Environment.
Reference Link.
http://downloadcenter.trendmicro.com/index.php?clk=tbl&clkval=4370®s=ae&lang_loc=2
Click to access vmware-vrealize-operations-management-packs-wp-en.pdf
















Pingback: Trend Deep Security – Customizing the alert configuration. | Techbrainblog